Permissions Required to Use CloudPilot AI
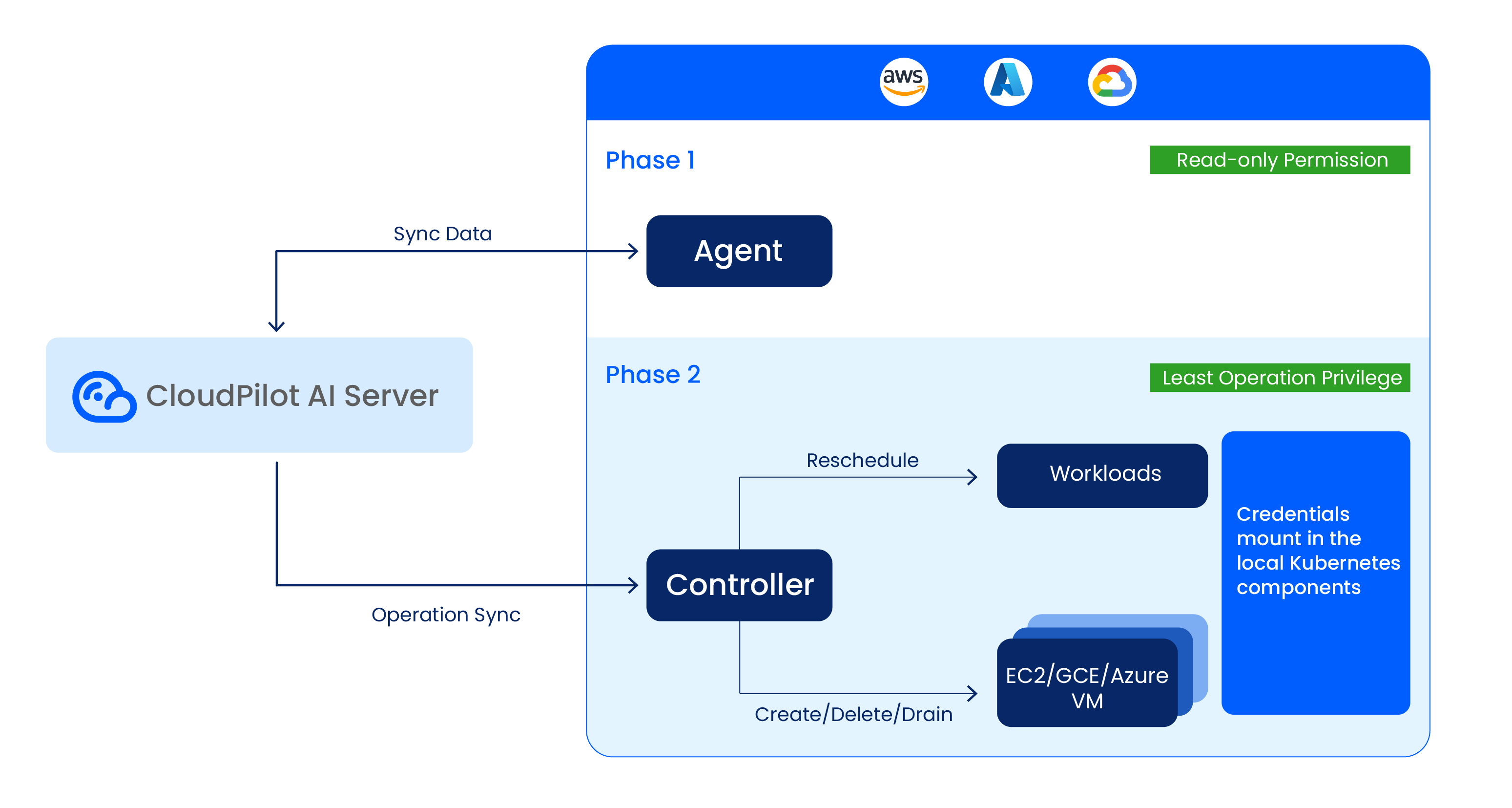
CloudPilot AI uses a two-phase installation to minimize security risk. Phase 1 requires read-only access to Kubernetes cluster resources. Phase 2 (optional) enables cluster optimization and requires additional Kubernetes RBAC and cloud provider permissions.
CloudPilot AI follows the principle of least privilege. You only need to grant CloudPilot AI the minimal permissions required to perform its operations — no more. Here is the overall architecture:
Note:: All credentials are mounted in your local cluster components and will not be stored or synced to our servers or the public internet.
Phase 1: Read-Only Permissions
During the first agent installation phase, CloudPilot AI deploys an agent that collects metadata about your Kubernetes cluster. This requires read-only access to core Kubernetes APIs across namespaces.
A ClusterRole and Role will be created with the following minimal permissions:
ClusterRole/Role Used in Phase 1
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
name: cloudpilot-agent-cluster-role
rules:
- apiGroups:
- "storage.k8s.io"
resources:
- "csinodes"
verbs:
- get
- list
- watch
- apiGroups:
- ""
resources:
- "namespaces"
- "nodes"
- "pods"
- "pods/log"
- "persistentvolumeclaims"
- "persistentvolumes"
- "services"
verbs:
- get
- list
- watch
- apiGroups:
- "apps"
resources:
- "deployments"
- "daemonsets"
- "statefulsets"
- "replicasets"
verbs:
- get
- list
- watch
- apiGroups:
- "policy"
resources:
- "poddisruptionbudgets"
verbs:
- get
- list
- watch
- apiGroups:
- "metrics.k8s.io"
resources:
- "pods"
- "nodes"
verbs:
- get
- list
- watch
- apiGroups:
- "apiextensions.k8s.io"
resources:
- "customresourcedefinitions"
verbs:
- get
- list
- watch
- apiGroups:
- "evpa.cloudpilot.ai"
resources:
- "autoscalingpolicyconfigurations"
- "autoscalingpolicyconfigurations/status"
verbs:
- get
- list
- watch
- apiGroups:
- "evpa.cloudpilot.ai"
resources:
- "autoscalingpolicies"
- "autoscalingpolicies/status"
- "recommendationpolicies"
verbs:
- create
- update
- list
- watch
- patch
- delete
---
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
name: cloudpilot-agent-role
namespace: cloudpilot
rules:
- apiGroups: ["coordination.k8s.io"]
resources: ["leases"]
verbs: ["get", "list", "create", "update", "patch", "watch"]This allows discovery and reporting of node configurations and workload configurations to calculate the optimization plan.
Phase 2: Additional Permissions for Cluster Optimization
If you proceed to Phase 2, CloudPilot AI will deploy components that actively optimize your cluster. This includes managing Kubernetes workloads and interacting with your cloud provider’s infrastructure APIs (e.g., EC2, Auto Scaling Groups).
Kubernetes RBAC Permissions
To manage Kubernetes resources, CloudPilot AI requires ClusterRole and Role definitions with the following permissions:
ClusterRole/Role Used in Phase 2 for AWS
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
name: cloudpilot-aws-optimizer
namespace: cloudpilot
rules:
- apiGroups:
- coordination.k8s.io
resources:
- leases
verbs:
- get
- watch
- apiGroups:
- ""
resources:
- configmaps
- secrets
verbs:
- get
- list
- watch
- apiGroups:
- ""
resourceNames:
- cloudpilot-aws-optimizer-cert
- cloudpilot-webhook
resources:
- secrets
verbs:
- update
- apiGroups:
- coordination.k8s.io
resourceNames:
- karpenter-leader-election
- cloudpilot-controller
- cloudpilot-workload-log-collector
resources:
- leases
verbs:
- patch
- update
- apiGroups:
- coordination.k8s.io
resources:
- leases
verbs:
- create
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
annotations:
meta.helm.sh/release-name: cloudpilot
meta.helm.sh/release-namespace: cloudpilot
name: cloudpilot-aws-optimizer
rules:
- apiGroups:
- karpenter.k8s.aws
resources:
- ec2nodeclasses
verbs:
- get
- list
- watch
- apiGroups:
- karpenter.k8s.aws
resources:
- ec2nodeclasses
- ec2nodeclasses/status
verbs:
- patch
- update
- apiGroups:
- admissionregistration.k8s.io
resources:
- mutatingwebhookconfigurations
- validatingwebhookconfigurations
verbs:
- get
- update
- list
- watch
- apiGroups:
- certificates.k8s.io
resources:
- '*'
verbs:
- get
- create
- update
- patch
- delete
- approve
- apiGroups:
- agent.cloudpilot.ai
resources:
- podmutations
verbs:
- get
- create
- update
- patch
- delete
- list
- watch
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
name: cloudpilot-aws-optimizer-admin
rules:
- apiGroups:
- karpenter.sh
resources:
- nodepools
- nodepools/status
- nodeclaims
- nodeclaims/status
verbs:
- get
- list
- watch
- create
- delete
- patch
- apiGroups:
- karpenter.k8s.aws
resources:
- ec2nodeclasses
verbs:
- get
- list
- watch
- create
- delete
- patch
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
name: cloudpilot-aws-optimizer-core
rules:
- apiGroups:
- karpenter.sh
resources:
- nodepools
- nodepools/status
- nodeclaims
- nodeclaims/status
verbs:
- get
- list
- watch
- apiGroups:
- ""
resources:
- pods
- pods/log
- nodes
- persistentvolumes
- persistentvolumeclaims
- replicationcontrollers
- namespaces
verbs:
- get
- list
- watch
- update
- patch
- apiGroups:
- storage.k8s.io
resources:
- storageclasses
- csinodes
- volumeattachments
verbs:
- get
- watch
- list
- apiGroups:
- apps
resources:
- daemonsets
- deployments
- replicasets
- statefulsets
verbs:
- list
- watch
- get
- update
- patch
- apiGroups:
- apiextensions.k8s.io
resources:
- customresourcedefinitions
verbs:
- get
- watch
- list
- apiGroups:
- policy
resources:
- poddisruptionbudgets
verbs:
- get
- list
- watch
- apiGroups:
- karpenter.sh
resources:
- nodeclaims
- nodeclaims/status
verbs:
- create
- delete
- update
- patch
- apiGroups:
- karpenter.sh
resources:
- nodepools
- nodepools/status
verbs:
- update
- patch
- apiGroups:
- ""
resources:
- events
verbs:
- create
- patch
- apiGroups:
- ""
resources:
- nodes
verbs:
- patch
- delete
- update
- apiGroups:
- ""
resources:
- pods/eviction
verbs:
- create
- apiGroups:
- ""
resources:
- pods
verbs:
- delete
- apiGroups:
- apiextensions.k8s.io
resourceNames:
- ec2nodeclasses.karpenter.k8s.aws
- nodepools.karpenter.sh
- nodeclaims.karpenter.sh
resources:
- customresourcedefinitions/status
verbs:
- patch
- apiGroups:
- apiextensions.k8s.io
resourceNames:
- ec2nodeclasses.karpenter.k8s.aws
- nodepools.karpenter.sh
- nodeclaims.karpenter.sh
resources:
- customresourcedefinitions
verbs:
- updateThese permissions is needed to ensure the stability of the system while doing operations like scaling, provisioning, and termination.
Cloud Provider Permissions
AWS IAM Permissions
In Phase 2, CloudPilot AI requires an IAM role with the following permissions:
AWS IAM Role Used in Phase 2
{
"Statement": [
{
"Effect": "Allow",
"Action": [
"autoscaling:DescribeAutoScalingGroups",
"autoscaling:DescribeAutoScalingInstances",
"autoscaling:DescribeLaunchConfigurations",
"autoscaling:DescribeScalingActivities",
"autoscaling:DescribeTags",
"ec2:DescribeImages",
"ec2:DescribeInstanceTypes",
"ec2:DescribeLaunchTemplateVersions",
"ec2:GetInstanceTypesFromInstanceRequirements",
"eks:DescribeNodegroup"
],
"Resource": ["*"]
},
{
"Effect": "Allow",
"Action": [
"autoscaling:SetDesiredCapacity",
"autoscaling:TerminateInstanceInAutoScalingGroup",
"autoscaling:UpdateAutoScalingGroup"
],
"Resource": ["*"]
},
{
"Action": [
"ssm:GetParameter",
"ec2:DescribeImages",
"ec2:RunInstances",
"ec2:DescribeSubnets",
"ec2:DescribeSecurityGroups",
"ec2:DescribeLaunchTemplates",
"ec2:DescribeInstances",
"ec2:DescribeInstanceTypes",
"ec2:DescribeInstanceTypeOfferings",
"ec2:DescribeAvailabilityZones",
"ec2:DeleteLaunchTemplate",
"ec2:CreateTags",
"ec2:CreateLaunchTemplate",
"ec2:CreateFleet",
"ec2:DescribeSpotPriceHistory",
"pricing:GetProducts",
"savingsplans:DescribeSavingsPlans",
"ec2:DescribeRegions"
],
"Effect": "Allow",
"Resource": "*",
"Sid": "CloudPilot"
},
{
"Action": "ec2:TerminateInstances",
"Condition": {
"StringLike": {
"ec2:ResourceTag/karpenter.sh/nodepool": "*"
}
},
"Effect": "Allow",
"Resource": "*",
"Sid": "ConditionalEC2Termination"
},
{
"Effect": "Allow",
"Action": "iam:PassRole",
"Resource": "arn:${AWS_PARTITION}:iam::${AWS_ACCOUNT_ID}:role/CloudPilotNodeRole-${CLUSTER_NAME}",
"Sid": "PassNodeIAMRole"
},
{
"Effect": "Allow",
"Action": "eks:DescribeCluster",
"Resource": "arn:${AWS_PARTITION}:eks:${AWS_REGION}:${AWS_ACCOUNT_ID}:cluster/${CLUSTER_NAME}",
"Sid": "EKSClusterEndpointLookup"
},
{
"Sid": "AllowScopedInstanceProfileCreationActions",
"Effect": "Allow",
"Resource": "*",
"Action": [
"iam:CreateInstanceProfile"
],
"Condition": {
"StringEquals": {
"aws:RequestTag/kubernetes.io/cluster/${CLUSTER_NAME}": "owned",
"aws:RequestTag/topology.kubernetes.io/region": "${AWS_REGION}"
},
"StringLike": {
"aws:RequestTag/karpenter.k8s.aws/ec2nodeclass": "*"
}
}
},
{
"Sid": "AllowScopedInstanceProfileTagActions",
"Effect": "Allow",
"Resource": "*",
"Action": [
"iam:TagInstanceProfile"
],
"Condition": {
"StringEquals": {
"aws:ResourceTag/kubernetes.io/cluster/${CLUSTER_NAME}": "owned",
"aws:ResourceTag/topology.kubernetes.io/region": "${AWS_REGION}",
"aws:RequestTag/kubernetes.io/cluster/${CLUSTER_NAME}": "owned",
"aws:RequestTag/topology.kubernetes.io/region": "${AWS_REGION}"
},
"StringLike": {
"aws:ResourceTag/karpenter.k8s.aws/ec2nodeclass": "*",
"aws:RequestTag/karpenter.k8s.aws/ec2nodeclass": "*"
}
}
},
{
"Sid": "AllowScopedInstanceProfileActions",
"Effect": "Allow",
"Resource": "*",
"Action": [
"iam:AddRoleToInstanceProfile",
"iam:RemoveRoleFromInstanceProfile",
"iam:DeleteInstanceProfile"
],
"Condition": {
"StringEquals": {
"aws:ResourceTag/kubernetes.io/cluster/${CLUSTER_NAME}": "owned",
"aws:ResourceTag/topology.kubernetes.io/region": "${AWS_REGION}"
},
"StringLike": {
"aws:ResourceTag/karpenter.k8s.aws/ec2nodeclass": "*"
}
}
},
{
"Sid": "AllowInstanceProfileReadActions",
"Effect": "Allow",
"Resource": "*",
"Action": "iam:GetInstanceProfile"
}
],
"Version": "2012-10-17"
}These permissions include access to EC2 and Auto Scaling Group APIs, used to manage compute capacity dynamically.
AlibabaCloud RAM Permissions
For AlibabaCloud, the required RAM policy is as follows:
AlibabaCloud RAM Permissions
{
"Version": "1",
"Statement": [
{
"Effect": "Allow",
"Action": [
"vpc:DescribeVSwitches",
"ecs:CreateAutoProvisioningGroup",
"ecs:DescribeSecurityGroups",
"ecs:DescribeAvailableResource",
"ecs:DescribeInstances",
"ecs:DescribeImages",
"cs:DescribeClusterDetail",
"cs:DescribeKubernetesVersionMetadata",
"cs:DescribeClusterAttachScripts",
"cs:DescribeClusterNodePools",
"ess:DescribeScalingGroups",
"ecs:AddTags",
"ram:CreateServiceLinkedRole"
],
"Resource": "*"
},
{
"Effect": "Allow",
"Action": "ecs:DeleteInstance",
"Resource": "*",
"Condition": {
"StringEquals": {
"acs:ResourceTag\/cloudpilot.ai\/managed": "true"
}
}
},
{
"Effect": "Allow",
"Action": "ess:DetachInstances",
"Resource": "*",
"Condition": {
"StringEquals": {
"acs:ResourceTag\/ack.aliyun.com": "${INTERNAL_CLUSTER_ID}"
}
}
}
]
}These permissions allow CloudPilot AI to interact with ECS and ScalingGroup APIs for node lifecycle management.
All cloud provider permissions align closely with those used by Karpenter, with the addition of access to scaling group APIs (AWS/AutoScalingGroup, AlibabaCloud/ScalingGroup) to enable existing node optimization.
Workload Autoscaler Additional Permissions
The Workload Autoscaler component will require a ClusterRole as well as a Role to manage the following:
- Workload Autoscaler related CRD resources
- Read and update workload resources such as Pod, Deployment, StatefulSet, and ReplicaSet
- Evict and resize Pod
- Manage the Workload Autoscaler’s CSR resources to support the issuance and renewal of TLS certificates for the Webhook
ClusterRole/Role Used in Phase 1
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
name: cloudpilot-workload-autoscaler-cluster-role
labels:
app.kubernetes.io/name: cloudpilot-workload-autoscaler
rules:
- apiGroups: [""]
resources: [pods, pods/eviction, pods/resize, pods/status]
verbs: [create, update, get, list, watch, patch, delete]
- apiGroups: ["apps"]
resources: [deployments, statefulsets, replicasets]
verbs: [get, list, watch, patch]
- apiGroups: ["evpa.cloudpilot.ai"]
resources:
- autoscalingpolicyconfigurations
- autoscalingpolicyconfigurations/status
verbs: [create, update, list, watch, patch, delete]
- apiGroups: ["evpa.cloudpilot.ai"]
resources:
- autoscalingpolicies
- autoscalingpolicies/status
- recommendationpolicies
verbs: [update, list, watch, patch]
- apiGroups: ["certificates.k8s.io"]
resources:
- certificatesigningrequests
- certificatesigningrequests/approval
verbs: [get, create, update]
- apiGroups: ["certificates.k8s.io"]
resources: [signers]
resourceNames: ["kubernetes.io/kubelet-serving", "beta.eks.amazonaws.com/app-serving"]
verbs: [approve]
- apiGroups: ["admissionregistration.k8s.io"]
resources: [mutatingwebhookconfigurations, validatingwebhookconfigurations]
verbs: [get, update, list, watch]
---
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
name: cloudpilot-workload-autoscaler-role
namespace: cloudpilot
labels:
app.kubernetes.io/name: cloudpilot-workload-autoscaler
rules:
- apiGroups: ["coordination.k8s.io"]
resources: [leases]
verbs: [get, create, update, watch]
- apiGroups: [""]
resources: [configmaps]
resourceNames: ["kube-root-ca.crt"]
verbs: [get, update]
- apiGroups: [""]
resources: [secrets]
verbs: [get, update, list, watch]
- apiGroups: [""]
resources: ["events"]
verbs: ["create", "patch"]Commitment to Privacy and Security
CloudPilot AI adheres strictly to data protection best practices. We access only the data necessary for operation and optimization, and we never request or retain unnecessary privileges.
By design, we reduce attack surfaces through scoped permissions and continuous review of access requirements. This ensures secure, compliant, and efficient operation within your environment.
For further assistance, feel free to reach out to us through our Slack channel .